By Paul Brett
Network visibility technology has been deployed by Service Providers and Enterprises for the last 15 years or so and remains as important to a successful business and IT outcomes today as it was then. The use cases for visibility technology have developed as networks have changed and are now able to provide new, incremental value to organizations.
The purpose of this series of blogs is to examine the value of visibility solutions and the reasons why they are essential for the success of contemporary IT initiatives and business outcomes. This first blog discusses the high-level value of visibility solutions and subsequent blogs will describe the value of specific use cases.
To start, let’s remind ourselves of several considerations for successful IT outcomes including:
- Most businesses and organizations depend on correctly functioning and secure networks for successful business and organizational performance
- Most networks have ‘blind spots’ which are caused by necessary network mechanisms such as tunneling encapsulation or encryption, where network traffic is not visible to monitoring or security products and represent service performance and security risks
- Every deployed technology should provide value to each of the three inter- related levels of Technology, IT Operations and Business Operations

Network visibility technology solutions can include many discrete products but the general broad product categories include:
- Physical and virtual network taps
- A network tap is a device that passively makes a copy of all network traffic packets without altering the data
- Physical and virtual Network Packet Brokers (NPB)
- NPBs receive the packets from the taps and filter and efficiently present them in various ways according to the needs of the network tools such as monitoring, analytics and security systems. Some NPBs can also generate metadata, provide Deep Packet Inspection (DPI) and packet capture
- Network probes
- Network probes can receive packets from NPBs as well as directly from the network and generate metadata records, such as Netflow, which are sent to network tools
- Network probes are often used for network troubleshooting and providing Extended Call Detail Records (xDR) to various analytics systems
- Network bypass taps
- A bypass tap is an appliance deployed together with an in-line active device such as an intrusion prevention system (IPS) or firewall (FW) and will automatically bypass those devices if they fail, and automatically restore the link when the failure is resolved
- A bypass tap can also load balance network traffic across multiple appliances to provide additional service resilience to an appliance failure
Functionally, visibility solutions observe all traffic traversing an organization’s network and copy relevant packets from any part of the network, including on premise, in the cloud and in virtual environments. The packets are passed efficiently to tools in the format they require when they need it, to ensure there are no monitoring ‘blind-spots’ and that the tools do not receive packets that are not required for their function. The tools thus have full visibility of all network traffic to allow them to execute their function effectively and efficiently to improve IT services’ performance and enhance data security while the tools’ loading is minimized to extend their lifespan, and they are able to monitor previously disparate and speed incompatible networks and services.
Originally, visibility solutions provided the option to remove geographically dispersed monitoring tools to manage networks by copying relevant network traffic and sending the copied traffic to a smaller number of centralized monitoring tools to provide a more effective monitoring solution at lower cost.
Over time, as networks have become more complex and higher performance, visibility use cases have expanded to include:
- Reduce risks to network performance and security Remove blind-spots from all network environments so that tools can help to increase network performance and reduce security risks in on-premise, cloud and virtual network environments
- Remove blind-spots through capabilities including network tunnel decapsulation and network packet decryption
- Minimize the number of network tools required Copy all relevant network traffic to most efficiently located tools or tool farms
- Use advanced efficiency features to filter out unnecessary network traffic so that network tools do not have to waste expensive storage and processing capacity
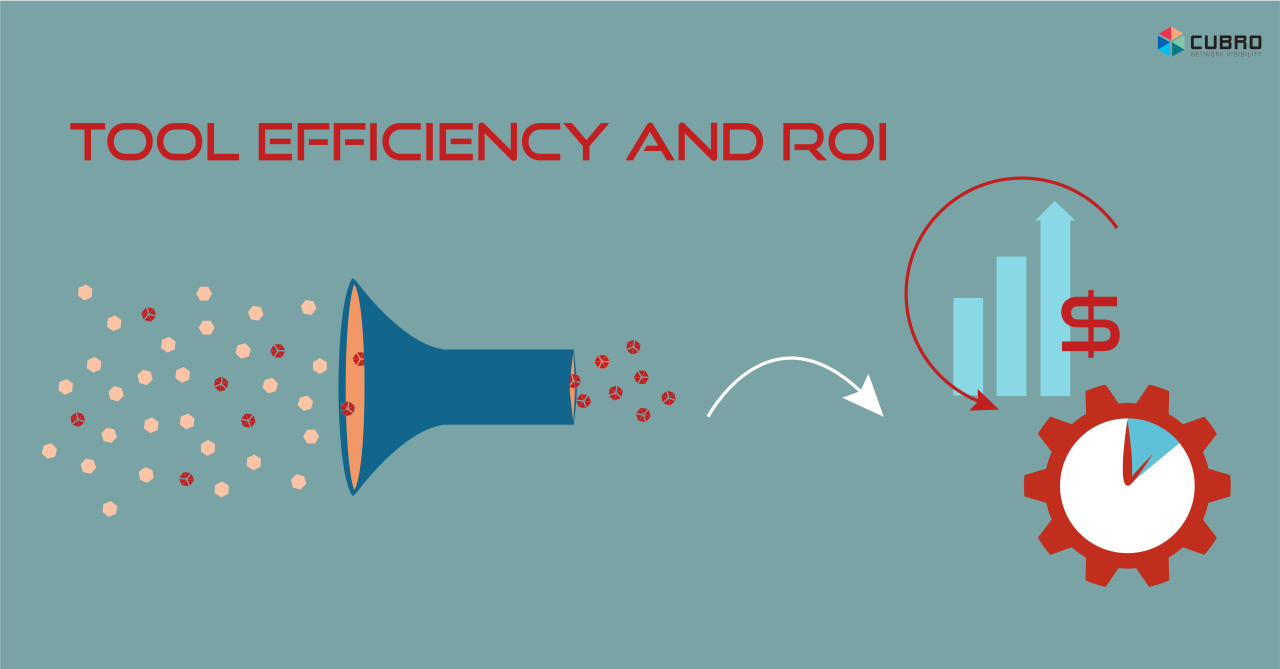
- Minimize the cost of network tools Network tools’ costs can be significant and often licenced according to capacity and/or usage which the visibility solution’s advanced efficiency features can reduce with subsequent reduction of licence costs and expansion rate
- Visibility solutions’ capabilities allow them to carry out functions at lower costs that previously were carried out by the more expensive network tools
- Improve business continuity and IT operational flexibility Bypass taps reduce the risk of network function, network tool or appliance outages by load balancing, and reduce the risk of service disruption through automatic failure bypass and restore.
- Bypass taps reduce the logistics required and time required for planned outages such as maintenance or upgrades
- NPB and network taps can interconnect tools and appliances of disparate speeds which means that tools do not have to be upgraded when network speeds are changed, for example, to increase tool and appliance deployment flexibility and cost management
- Improve network security and analytics NPB DPI capability provides enriched metadata for analytics tools to identify network trends and behaviour, and for security tools to identify security risks through unusual network traffic behaviour
These use cases demonstrate some of the value that visibility technology can provide to network tool effectiveness and improved network technology infrastructure performance and security. The Technology value provided improves IT services’ quality and reliability, operational flexibility, higher ROI and budget management. Typically, these IT Operational benefits help the Business to improve customer retention and acquisition by boosting customer services, protecting shareholder value by securing data and maintaining regulatory compliance, and increasing business flexibility while managing costs.
Many of the current IT and technology initiatives in both Service Provider and Enterprise organizations, such as 5G/4G/3G Service Assurance, SDN/NFV, Digital Transformation, Virtualization, and SD WAN, are being deployed to improve competitive advantage while maintaining security and managing costs – and all of them introduce new and incremental network performance and security risk creating network blind-spots – which can be resolved by deploying network visibility solutions.
The old adage – you can only manage what you can see – remains true, and the value that visibility technology can provide for IT Technology, IT Operations and Business Operations continues to be essential for the successful outcomes of these and other forthcoming technology initiatives.
