Gartner defines edge computing as solutions that facilitate data processing at or near the source of data generation. For example, in the context of the Internet of Things (IoT), the sources of data generation are usually things with sensors or embedded devices. Edge computing serves as the decentralized extension of the campus networks, cellular networks, data center networks or the cloud. (Source: https://www.gartner.com/smarterwithgartner/what-edge-computing-means-for-infrastructure-and-operations-leaders)
MEC is often advertised as an independent entity, but in practice, the processing of data for both the User Plane (UP) and Control Plane (CP) is still centralized. In other words, part of the processing is executed at the Edge site while the central site does the aggregation and analysis of the whole data. Many probe systems operate this way by collecting the data on the site, anonymizing the data and sending the data for central processing.
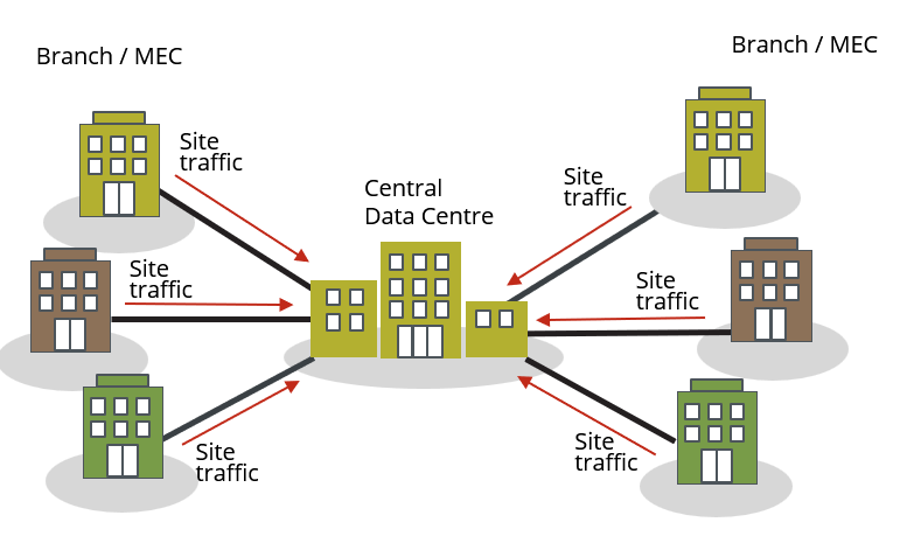
Unlike with a direct cable connection, this data is sent over the company’s data network using TCP/IP. To comply with data security and privacy, this solution needs a more secure method of sharing the data. Cubro’s solution uses a VPN connection from the sites to the central data center.
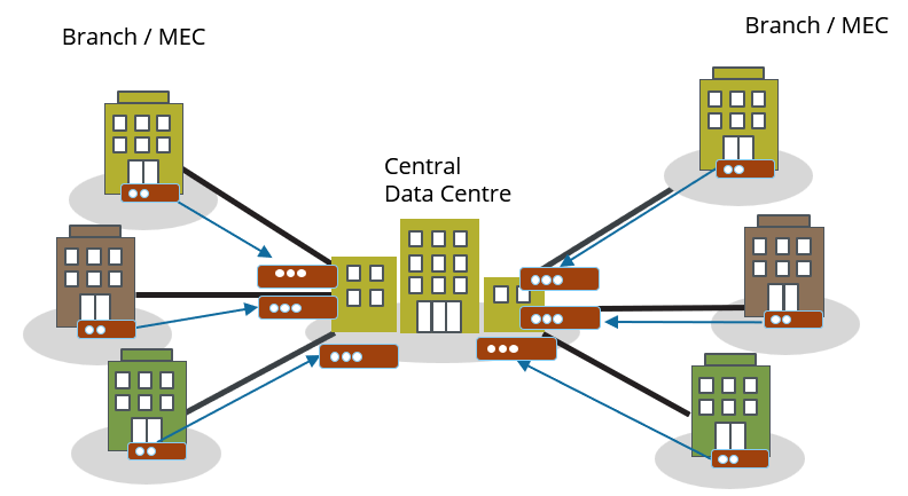
Cubro’s comprehensive approach integrates tapping, network packet brokering, packet routing, and data encryption through VPN services. Although VPN connections are considered slow, Cubro’s VPN has been tested to provide 300 Mbps. Cubro uses Omnia120 at both ends, one Omnia120 is for establishing a secure, encrypted VPN connection while the receiving end removes the VPN tunnel and provides the data to the recipient without encryption. This connection is established by using a physical cable.
Omnia120 has a unique architecture with Silicone on Chip and two ARM processors. One ARM CPU is used for the VPN connection while the chipset and second ARM CPU can be used for other tasks such as packet deduplication and packet filtering including Regex or the user can use, for example, Wireshark.
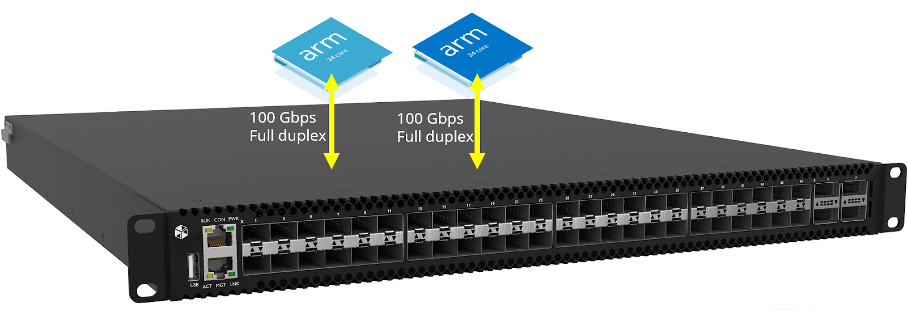
Enterprises may also use Omnic, Cubro SmartNIC, with the same software.

Communication to the Omnia120 and Omnic is also encrypted using certificates that authenticate the user and encrypt the traffic.
As the prominence of MEC and distributed processing grows within enterprises and CSPs, data transfer is streamlined and bolstered by enhanced security measures. Cubro’s expertise extends to facilitating GDPR compliance by addressing Personally Identifiable Information (PII) concerns across the data chain.
